We have been selected to perform our HARDWARE HACKING TRAINING WITH HARDSPLOIT FRAMEWORK at the next BlackHat USA 2016 , at the end of July in Las Vegas
https://www.blackhat.com/us-16/training/hardware-hacking-with-hardsploit-framework.html
Book your seat as soon as possible : https://blackhat.tech.ubm.com/usa/2016/?
Content
Tired of watching hardware products getting hacked every day without having your part of fun ? Don’t worry it will not be the case anymore! This training teaches you hardware hacking in its most pragmatic aspects by using both theory and practice (hands-on). It follows a simple (but efficient) training methodology based on a “Discover / Analyze / Attack & Protect” guideline that can be applied to any kind of hardware product (Internet of Insecure Things included). This course smartly mix methods and tools in order to give you all the necessary knowledge to be able to perform hardware security audits by yourself. The last part but not least our exclusive “Capture The Drone” hands-on to complete the training by practicing what you have learned in an attack/defense scenario featuring our favorite small flying things. Each student will receive a Hardsploit hardware hacking tool, with a value of 300 €


Agenda
MODULE 1: Hardware Hacking 101
- Review of electronic basics, motivations for hardware hacking, brief history of hacking security talks
- Hardware security vulnerabilities review, offensive & defensive aspects
- Practical cases for hardware hacking analysis
- Hands-on: Basic electronic components use & fingerprinting
MODULE 2: How to access to the hardware for hacking / audit purpose
- Review of methods & tools to perform hardware security audits
- Create your own audit plan, differences with software pentesting
- Hands-on: Practice exercises with hardware auditing tools
- Hands-on: How to acquire electronic signals, tools & demonstration
MODULE 3: How to access the software inside de hardware
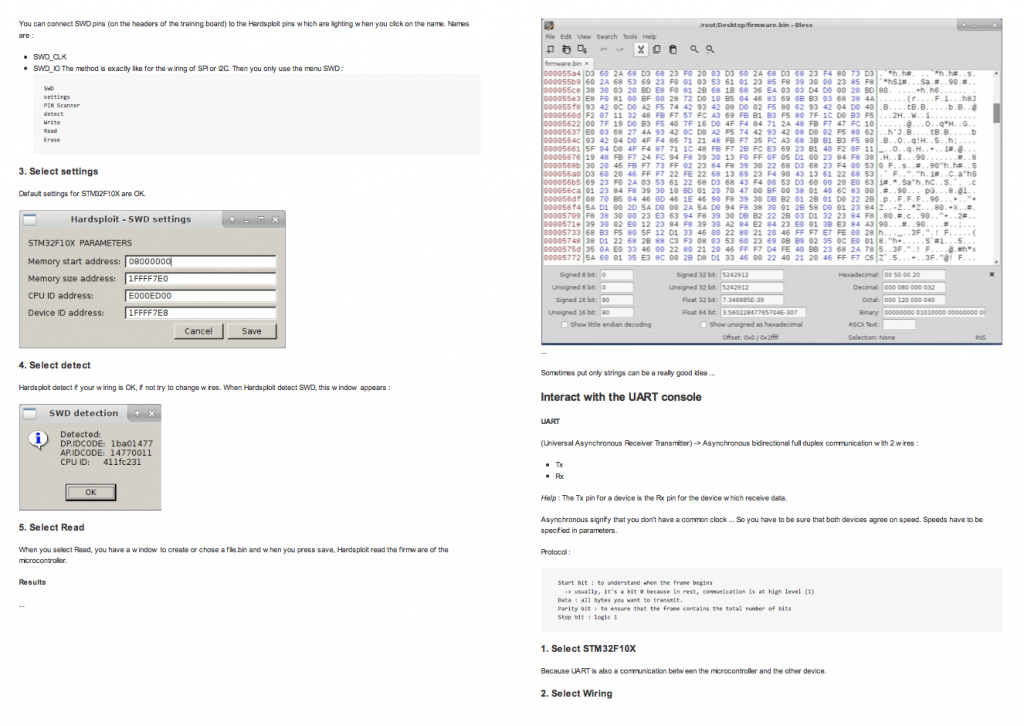
- Embedded system architecture presentation (Microcontroller, FPGA), direct access to the software via I/O interfaces (JTAG / SWD, I²C, SPI, UART, RF (ISM Band), etc.)
- Hands-on: Firmware dumping trough different types of interfaces
- Hands-on: Buffer overflow attacks on embedded system
- DEMO: Power analysis attacks – Indirect access to the software or sensitive content via side channel attacks
MODULE 4: Complete hacking lab
- Full hands-on session to apply practical case on our vulnerable embedded system
- Identifying electronic components
- Electronic signals acquisition
- Bus signals interception and analysis
- Modifying and dumping firmware via JTAG debug function (and other I/O access)
- Fuzzing external interface to spot basic vulnerabilities in embedded system
- Exploiting vulnerabilities during an hardware security audit
MODULE 5: How to protect your hardware products
- Secure Design and Development Life Cycle (SDLC)
- Review of hardware security best practices to limit the risks
- Hands-on: Limit JTAG access, limit software vulnerabilities at embedded level
- Review of protections against side channel attack (limit power analysis attacks)
MODULE 6: SDR Hacking
- SDR hacking methodology (Software Defined Radio)
- Tools of trade (GNURadio, hardware products, etc.)
- Hands-on: How to hack a wireless protocol
MODULE 7: Fuzzing hardware devices
- Fuzzing lab methodology
- Hands-on: Create your own fuzzing lab
- Hands-on: Hack a device using a fuzzing attacks
MODULE 8: CTD Capture The Drone
- Attack / Defense practical scenario in team (Capture the Flag Mode)
- Each team have a mini-drone.
- Defend your drone and take down the other by using the tools and methods learned
- The winning team is the one with the higher flying time
WHO SHOULD TAKE THIS COURSE
- This course is intended for everyone having an interest in security aspects related to hardware products or embedded devices.
- Electronic enthusiasts and professionals
- IT security professionals
STUDENT REQUIREMENTS
We have prepared and updated this training to satisfy both beginners and advanced profiles. No prior electronics knowledge is required
WHAT STUDENTS SHOULD BRING
To complete this training, students will need to bring their laptop with:
- Minimum 50 Gb free disk space
- Virtualization solution (e.g VMWARE, Virtualbox)
- Working USB port
We will provide all the software related part and the other tools.
WHAT STUDENTS WILL BE PROVIDED WITH
- Full copy of the course
- The vulnerable electronic board used during the course
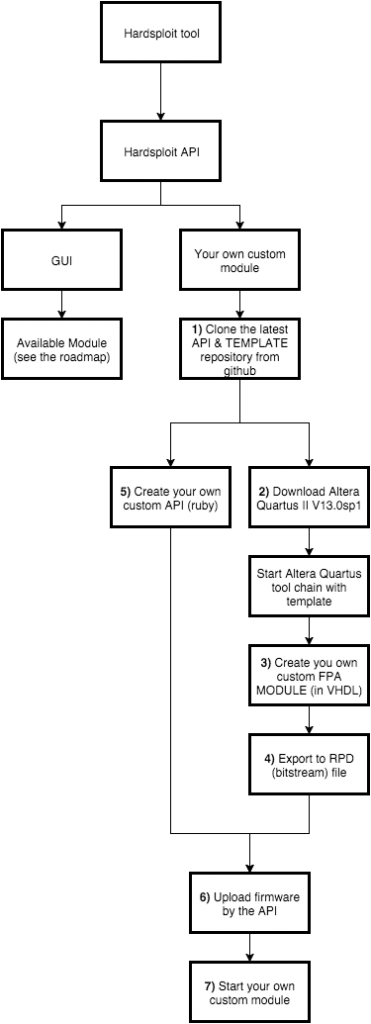
- One Hardsploit electronic board (see hardsploit.io)
- Few more goodies
TRAINERS
Yann ALLAIN is the founder and current director of the OPALE SECURITY company (www.opale-security.com). He graduated from a computer and electronic engineering school (Polytech-Universite Pierre et Marie Curie). After a time in the electronic industry as an engineer in embedded system conception, he made a career move towards IT. He started as a production manager for a company in the financial sector (Private Banking), and evolved towards IT security when he became part of the ACCOR group. He was in charge of applicative security for the group. He has a 20 years experience, 16 of which dedicated to IT system and embedded system security. OPALE SECURITY deals with research projects linked, amongst other things to the security of embedded systems. We are the project leader of Hardsploit : a Framework like Metasploit but for Hardware Hacking (Hardsploit.io)
Julien Moinard, an electronics Engineer with a solid background in this field (over 8 years) associated with many personal and professional experiments in the field of Microcontrollers. Furthermore, he contributes to the Hardsploit project as a project leader. He is also a senior hardware Pentester in OPALE SECURITY and trainer for Hack In Paris