They control our daily life and modern society cannot operate without them, but ironically, their security aspects remained underestimated.
As they grow, it is legitimate to wonder if the IT security community and industries are prepared to secure or audit this type of equipment. These technical devices are at the heart of what is called today “Internet of every things”.
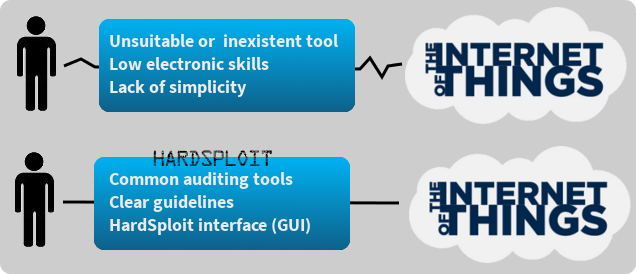
We know that the technical knowledge needed to assess the security level of electronic equipment aren’t generally acquired by stakeholders (industry, software or IT security consultants, software pentesters etc.). This type of audit requires a wide range of electronics skills like analog signal processing, FPGA or the use of specific measurement tools (oscilloscope, logic analyzer, etc.). These skills are not part of those which are generally teach to people who choose to specialize in computer security.
Threats are (also) below the OS now !
After the emergence of application layers threats (Web and mobile in particular), specialists strengthened their defense. They have developed tools, methods and processes to improve the security level of Web applications. Even if we have a long way to go, the will to act is present.
Malicious actors are aware of this weakness !
As a result they move their attentions to other less secure intrusion vectors such as hardware, embedded systems and/or microchip itself . Why? Because they are the basis of any equipment (public or pro) and the attack surface is therefore larger. In addition, there is no built in (or few) basic security functions , like antivirus or firewall, inside those hardware devices. So the malicious actors have less barriers that can stop them.
Hardware security is different than software security:
The most surprising (disturbing?) fact is that our industrials and our security experts do not mastered secure design techniques or audit/pentest methodology related to hardware systems.
There is a gap between the threat and the operational response capacity of the actors in this field. Therefore the risks of attacks increased on the processed data in Internet of things world (personal, sensitive device supervision, industrial process, HealthCare products …).
Why we choose to create HardSploit :
It is clear that something is needed to help the security community to evaluate, audit and/or control the embedded systems security level.
- Facilitate the audit of electronic systems for industry ‘security’ workers (Consultant, Auditor, Pentesters, product designer etc.)
- Increase the level of security (and trust!) of new communicating products designed by industry
All-in-one tool for Hardware pentest
- Sniffer,
- Scanner,
- Proxy,
- Interact,
- Dump memory
- …
Hardsploit Modules will let Hardware pentester to intercept, replay and/or and send data via each type of electronic bus used by the Hardware Target. The Level of interaction that pen-testers will have depend on the electronic bus features…
- JTAG, SPI, I2C‘s,
- Parallel address & data bus on chip,
- and more others to come in futur…
No more stress with that tremendous part of Hardware pen testing : You will know what need to be connected and where !
- GUI will display the pin organization (Pin OUT) of the targeted chip.
- GUI will guide you throughout the wiring process between Hardsploit Connector and the target
- GUI will control a set of LED that will be turn ON and OFF to easy let you find the right Hardsploit Pin Connector to connect to your target
The software part of the project will help conducting an end-to-end security audit. It will be compatible (integrated) with existing tools such as Metasploit. We will offer integration with other API in the future.
Our ambition is to provide a tool equivalent to those of the company Qualys or Nessus (Vulnerability Scanner) or the Metasploit framework but in the domain of embedded / electronic.



Leave a Reply
You must be logged in to post a comment.