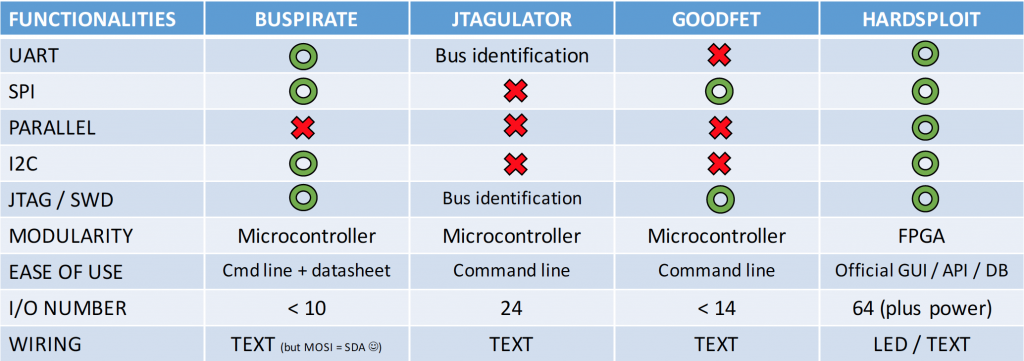
As a lot of people ask us what is the differences between our tool and X or Y
We create a quick review of Hardsploit’s features VS other (great !) hardware hacking tools. According to our understanding, we propose the following review:
Keep in mind that this list of tools is, of course, not exhaustive.
(Don’t hesitate to contact us if we made some mistakes)


What is the difference between this and saleae?
Hello Julio,
First thank you for your interest in Hardsploit.
A logic analyzer aim at recording and decoding bus protocols. You have to synchronize your tool with a good timing to catch a specific communication. Moreover you will not be able to create a signal. With Hardsploit you directly interact with the component by using read and write operations, selecting the information you want, when you want.
You don’t just “sniff” what’s going on.
For your information, we are currently working on integrating sniffing actions for I²C and SPI protocols like you can see on our roadmap here:
http://hardsploit.io/roadmap/
Version 2 (Q1 2016)
I2C sniffing (shot of 4000 bytes up to 1 Mhz)
SPI sniffing (shot of 8000 bytes up to 25 Mhz in half duplex mode or a shot of 4000 bytes in full duplex mode)
We are also planning on a RAM physical module (to plug on the existing pin) to improve the sniffer efficiency.
If you need more information about Hardsploit, please feel free to ask.
The Hardsploit team.